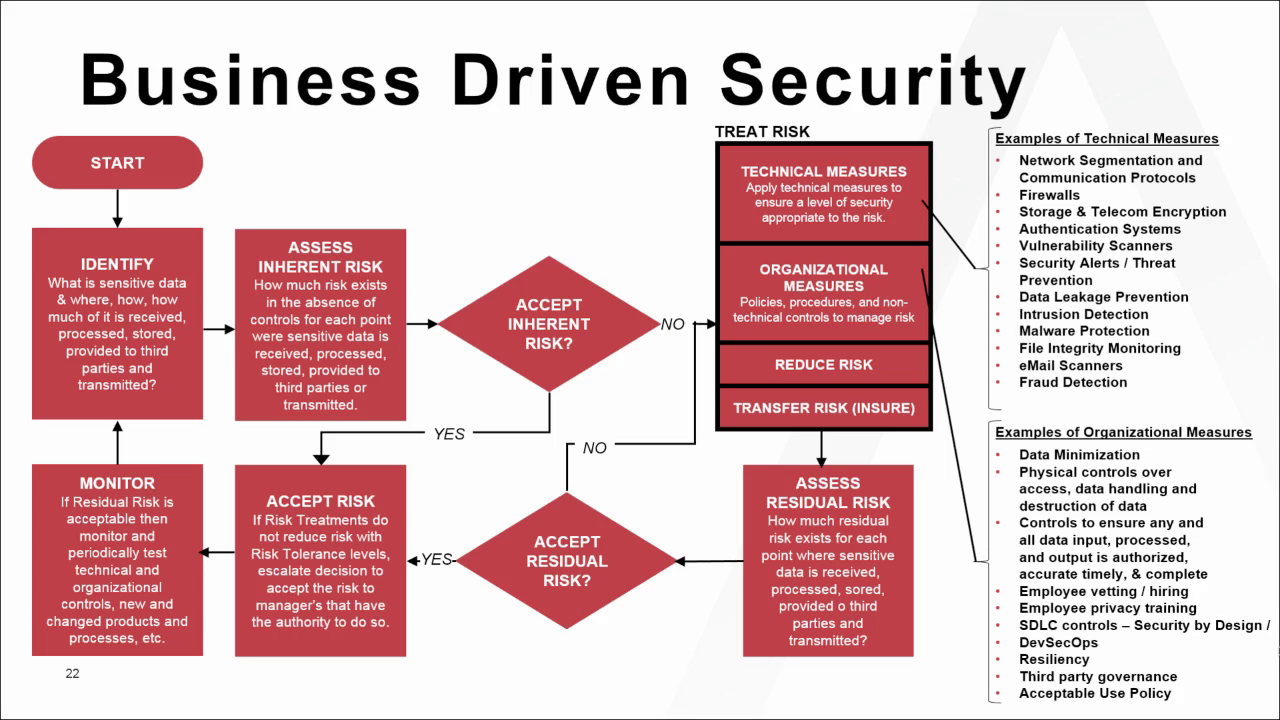
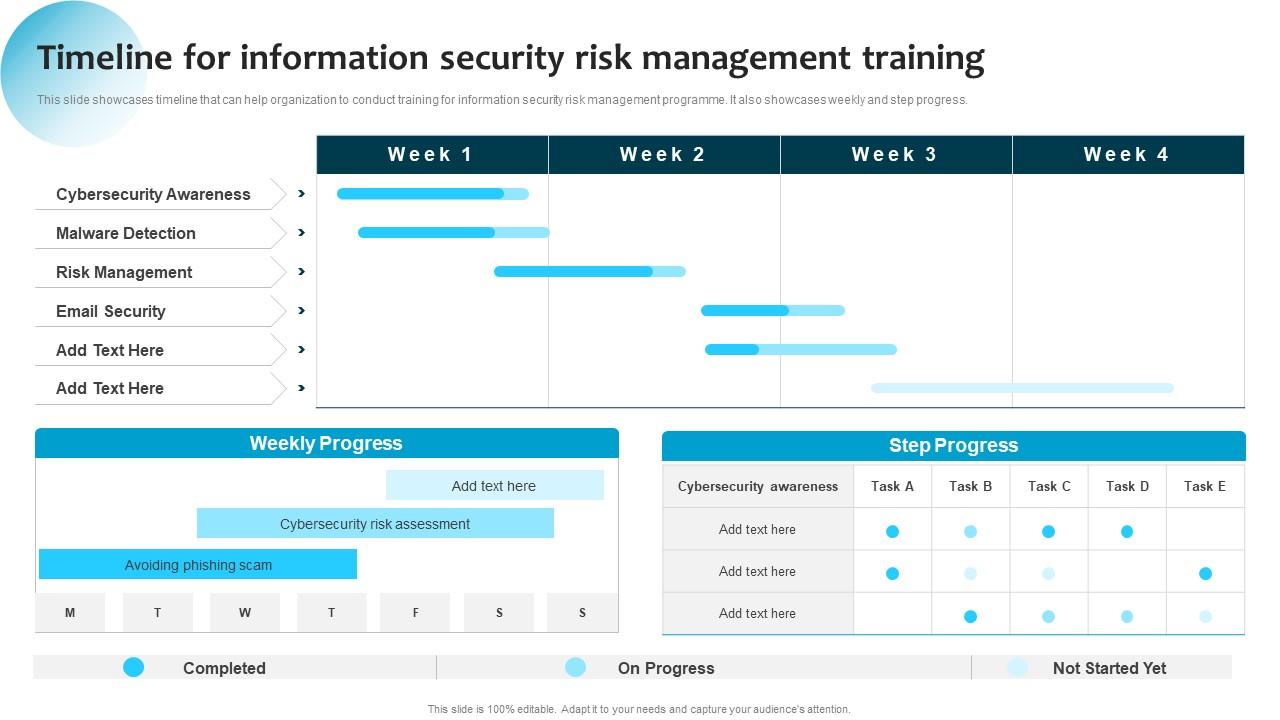
PPT – Information Security and Risk Management Training PowerPoint presentation | free to download - id: 8b7c35-MTUwZ
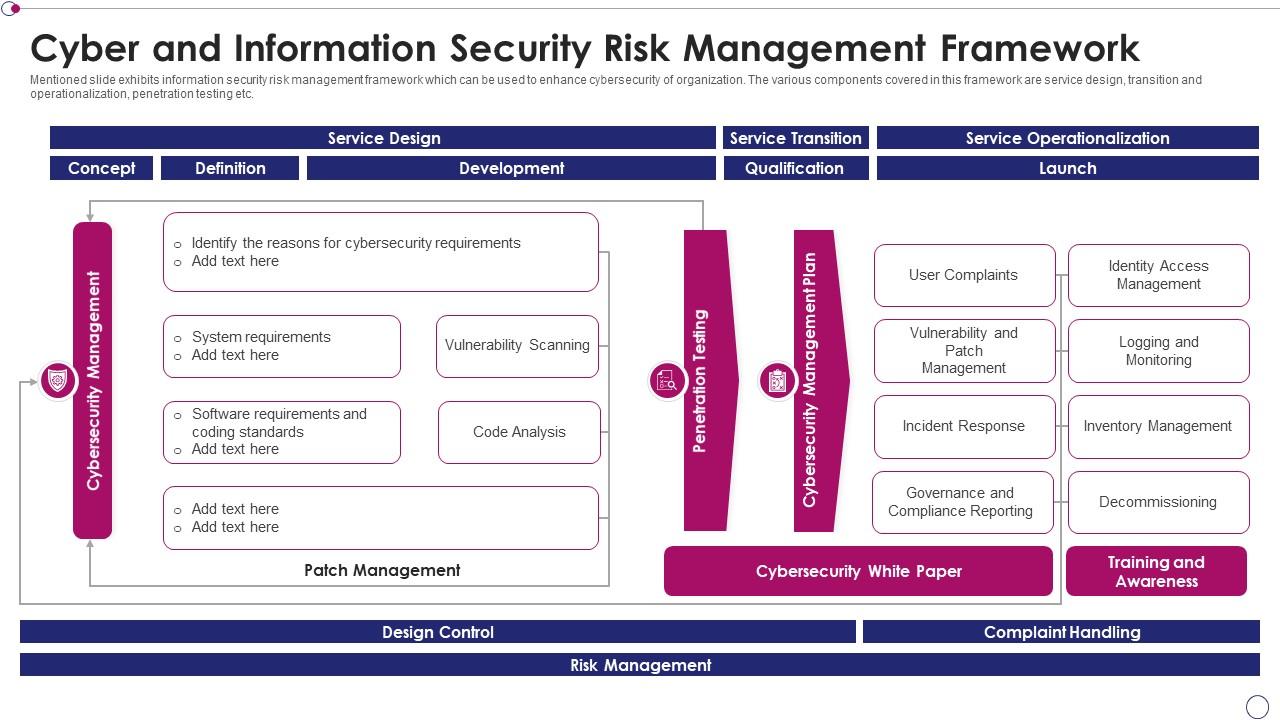
Cyber And Information Security Risk Management Framework | Presentation Graphics | Presentation PowerPoint Example | Slide Templates

IT and Cybersecurity Risk Management Essential Training Online Class | LinkedIn Learning, formerly Lynda.com